- Generate X 509 Certificate From Public Key Online Login
- Generate X 509 Certificate From Public Key Online Game
Generate a self-signed certificate for your web site, generate certificate with altname openssl online, x.509 tutorial 8gwifi.org - Crypto Playground Follow Me for Updates Online Linux Terminal.
- In One Sentence: What is aCertificate?
- What Applications use Certificates?
- How do I get a Certificate?
- What is Inside an X.509 Certificate?
- What Java API Can Be Used to Access and ManageCertificates?
- What Java Tool Can Generate, Display, Import,and Export X.509 Certificates?
In One Sentence: What is aCertificate?
A public-key certificate is a digitally signed statementfrom one entity, saying that the public key (and some otherinformation) of another entity has some specific value.
Let us expand on some of the key terms used in thissentence:
- Public Keys
- These are numbers associated with a particular entity, and areintended to be known to everyone who needs to have trustedinteractions with that entity. Public keys are used to verifysignatures.
- Digitally Signed
- If some data is digitally signed it has been stored withthe 'identity' of an entity, and a signature that proves thatentity knows about the data. The data is rendered unforgeable bysigning with the entitys' private key.
- Identity
- A known way of addressing an entity. In some systems theidentity is the public key, in others it can be anything from aUNIX UID to an Email address to an X.509 Distinguished Name.
- Signature
- A signature is computed over some data using the private key ofan entity (the signer).
- Private Keys
- These are numbers, each of which is supposed to be known onlyto the particular entity whose private key it is (that is, it'ssupposed to be kept secret). Private and public keys exist in pairsin all public key cryptography systems (also referred to as 'publickey crypto systems'). In a typical public key crypto system, suchas DSA, a private key corresponds to exactly one public key.Private keys are used to compute signatures.
- Entity
- An entity is a person, organization, program, computer,business, bank, or something else you are trusting to somedegree.
Basically, public key cryptography requires access to users'public keys. In a large-scale networked environment it isimpossible to guarantee that prior relationships betweencommunicating entities have been established or that a trustedrepository exists with all used public keys. Certificates wereinvented as a solution to this public key distribution problem. Nowa Certification Authority (CA) can act as a Trusted ThirdParty. CAs are entities (e.g., businesses) that are trusted tosign (issue) certificates for other entities. It is assumed thatCAs will only create valid and reliable certificates as they arebound by legal agreements. There are many public CertificationAuthorities, such as VeriSign, Thawte, Entrust, and so on. You can also runyour own Certification Authority using products such as theNetscape/Microsoft Certificate Servers or the Entrust CA productfor your organization.
What Applications useCertificates?
Probably the most widely visible application of X.509certificates today is in web browsers (such as Mozilla Firefox andMicrosoft Internet Explorer) that support the TLS protocol. TLS(Transport Layer Security) is a security protocol that providesprivacy and authentication for your network traffic. These browserscan only use this protocol with web servers that support TLS.
Other technologies that rely on X.509 certificates include:
- Various code-signing schemes, such as signed Java ARchives, andMicrosoft Authenticode.
- Various secure E-Mail standards, such as PEM and S/MIME.
- E-Commerce protocols, such as SET.
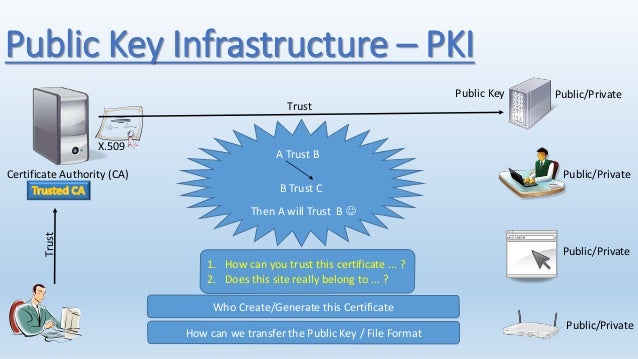
How do I Get aCertificate?
There are two basic techniques used to get certificates:
- you can create one yourself (using the right tools, such askeytool), or
- you can ask a Certification Authority to issue you one (eitherdirectly or using a tool such as keytool to generate therequest).
- Matched public and private keys, generated using somespecial tools (such as keytool), or a browser.Only the public key is ever shown to anyone else.The private key is used to sign data; if someone knows your privatekey, they can masquerade as you ... perhaps forging legal documentsattributed to you!
- You need to provide information about the entity beingcertified (e.g., you). This normally includes information suchas your name and organizational address. If you ask a CA to issue acertificate for you, you will normally need to provide proof toshow correctness of the information.
If you are asking a CA to issue you a certificate, you provideyour public key and some information about you. You'll use a tool(such as keytool or a browser that supportsCertificate Signing Request generation). to digitally sign thisinformation, and send it to the CA. The CA will then generate thecertificate and return it.
If you're generating the certificate yourself, you'll take thatsame information, add a little more (dates during which thecertificate is valid, a serial number), and just create thecertificate using some tool (such as keytool).Not everyone will accept self-signed certificates; one part of thevalue provided by a CA is to serve as a neutral and trustedintroduction service, based in part on their verificationrequirements, which are openly published in their CertificationService Practices (CSP).
What's Inside an X.509Certificate?
The X.509 standard defines what information can go into acertificate, and describes how to write it down (the data format).All X.509 certificates have the following data, in addition to thesignature:
- Version
- This identifies which version of the X.509 standard applies tothis certificate, which affects what information can be specifiedin it. Thus far, three versions are defined.
- Serial Number
- The entity that created the certificate is responsible forassigning it a serial number to distinguish it from othercertificates it issues. This information is used in numerous ways,for example when a certificate is revoked its serial number isplaced in a Certificate Revocation List (CRL).
- Signature Algorithm Identifier
- This identifies the algorithm used by the CA to sign thecertificate.
- Issuer Name
- The X.500 name of the entity that signed the certificate. Thisis normally a CA. Using this certificate implies trusting theentity that signed this certificate. (Note that in some cases, suchas root or top-level CA certificates, the issuer signs itsown certificate.)
- Validity Period
- Each certificate is valid only for a limited amount of time.This period is described by a start date and time and an end dateand time, and can be as short as a few seconds or almost as long asa century. The validity period chosen depends on a number offactors, such as the strength of the private key used to sign thecertificate or the amount one is willing to pay for a certificate.This is the expected period that entities can rely on the publicvalue, if the associated private key has not been compromised.
- Subject Name
- The name of the entity whose public key the certificateidentifies. This name uses the X.500 standard, so it is intended tobe unique across the Internet. This is the Distinguished Name (DN)of the entity, for example,(These refer to the subject's Common Name, Organizational Unit,Organization, and Country.)
- Subject Public Key Information
- This is the public key of the entity being named, together withan algorithm identifier which specifies which public key cryptosystem this key belongs to and any associated key parameters.
X.509 Version 1 has been available since 1988, is widelydeployed, and is the most generic.
X.509 Version 2 introduced the concept of subject andissuer unique identifiers to handle the possibility of reuse ofsubject and/or issuer names over time. Most certificate profiledocuments strongly recommend that names not be reused, and thatcertificates should not make use of unique identifiers. Version 2certificates are not widely used.
X.509 Version 3 is the most recent (1996) and supportsthe notion of extensions, whereby anyone can define an extensionand include it in the certificate. Some common extensions in usetoday are: KeyUsage (limits the use of the keys toparticular purposes such as 'signing-only') andAlternativeNames (allows other identities to also beassociated with this public key, e.g. DNS names, Email addresses,IP addresses). Extensions can be marked critical to indicatethat the extension should be checked and enforced/used. Forexample, if a certificate has the KeyUsage extension markedcritical and set to 'keyCertSign' then if this certificate ispresented during SSL communication, it should be rejected, as thecertificate extension indicates that the associated private keyshould only be used for signing certificates and not for SSLuse.
All the data in a certificate is encoded using two relatedstandards called ASN.1/DER. Abstract Syntax Notation 1describes data. The Definite Encoding Rules describe asingle way to store and transfer that data. People have been knownto describe this combination simultaneously as 'powerful andflexible' and as 'cryptic and awkward'.
The IETF PKIXworking group is in the process of defining standards for theInternet Public Key Infrastructure. We are closely following theirwork, and support the X.509 Certificate and CRL Profile,which is specified in RFC 3280.
What Java API Can Be Used to Access andManage Certificates?
The Certificate API, found in thejava.security.certpackage, includes the following:- the CertificateFactory class defines the functionalityof a certificate factory, which is used to generate certificate,certificate revocation list (CRL), and certification path objectsfrom their encoding.
- the Certificate class is an abstract class for managinga variety of certificates. It is an abstraction for certificatesthat have different formats but important common uses. For example,different types of certificates, such as X.509 and PGP, sharegeneral certificate functionality (like encoding and verifying) andsome types of information like public key.
- the CRL class is an abstract class for managing avariety of Certificate Revocation Lists (CRLs).
- the X509Certificate class is an abstract class for X.509Certificates. It provides a standard way to access all theattributes of an X.509 certificate.
- the X509Extension interface is an interface for an X.509extension. The extensions defined for X.509 v3 certificates and v2CRLs (Certificate Revocation Lists) provide mechanisms forassociating additional attributes with users or public keys, suchas for managing the certification hierarchy, and for managing CRLdistribution.
- the X509CRL class is an abstract class for an X.509Certificate Revocation List (CRL). A CRL is a time-stamped listidentifying revoked certificates. It is signed by a CertificationAuthority (CA) and made freely available in a publicrepository.
- the X509CRLEntry class is an abstract class for a CRLentry.
What Java Tool Can Generate,Display, Import, and Export X.509 Certificates?
There is a tool named keytool ( for Solaris, Linux, or Mac OS X)( for Windows ) that can beused to create public/private key pairs and self-signed X.509 v3certificates, and to manage keystores. Keys and certificates areused to digitally sign your Java applications and applets (see thejarsigner (forSolaris, Linux, or Mac OS X)(forWindows) tool).A keystore is a protected database that holds keys andcertificates. Access to a keystore is guarded by a password(defined at the time the keystore is created, by the person whocreates the keystore, and changeable only when providing thecurrent password). In addition, each private key in a keystore canbe guarded by its own password.
Using keytool, it is possible to display, import, andexport X.509 v1, v2, and v3 certificates stored as files, and togenerate new self-signed v3 certificates. For examples, see the'EXAMPLES' section of the keytool documentation ( for Solaris, Linux,or Mac OS X ) (for Windows).

You can use the classes in the System.Security.Cryptography.Xml namespace to encrypt an element within an XML document. XML Encryption is a standard way to exchange or store encrypted XML data, without worrying about the data being easily read. For more information about the XML Encryption standard, see the World Wide Web Consortium (W3C) specification for XML Encryption located at https://www.w3.org/TR/xmldsig-core/.
You can use XML Encryption to replace any XML element or document with an <EncryptedData> element that contains the encrypted XML data. The <EncryptedData> element can contain sub elements that include information about the keys and processes used during encryption. XML Encryption allows a document to contain multiple encrypted elements and allows an element to be encrypted multiple times. The code example in this procedure shows you how to create an <EncryptedData> element along with several other sub elements that you can use later during decryption.
This example encrypts an XML element using two keys. It generates a test X.509 certificate using the Certificate Creation Tool (Makecert.exe) and saves the certificate to a certificate store. The example then programmatically retrieves the certificate and uses it to encrypt an XML element using the Encrypt method. Internally, the Encrypt method creates a separate session key and uses it to encrypt the XML document. This method encrypts the session key and saves it along with the encrypted XML within a new <EncryptedData> element.
To decrypt the XML element, simply call the DecryptDocument method, which automatically retrieves the X.509 certificate from the store and performs the necessary decryption. For more information about how to decrypt an XML element that was encrypted using this procedure, see How to: Decrypt XML Elements with X.509 Certificates.
Generate X 509 Certificate From Public Key Online Login
This example is appropriate for situations where multiple applications need to share encrypted data or where an application needs to save encrypted data between the times that it runs.
To encrypt an XML element with an X.509 certificate
Use the Certificate Creation Tool (Makecert.exe) to generate a test X.509 certificate and place it in the local user store. You must generate an exchange key and you must make the key exportable. Run the following command:
Create an X509Store object and initialize it to open the current user store.
Open the store in read-only mode.
Initialize an X509Certificate2Collection with all of the certificates in the store.
Enumerate through the certificates in the store and find the certificate with the appropriate name. In this example, the certificate is named
'CN=XML_ENC_TEST_CERT'.Close the store after the certificate is located.
Create an XmlDocument object by loading an XML file from disk. The XmlDocument object contains the XML element to encrypt.
Find the specified element in the XmlDocument object and create a new XmlElement object to represent the element you want to encrypt. In this example, the
'creditcard'element is encrypted.Create a new instance of the EncryptedXml class and use it to encrypt the specified element using the X.509 certificate. The Encrypt method returns the encrypted element as an EncryptedData object.
Replace the element from the original XmlDocument object with the EncryptedData element.
Save the XmlDocument object.
Generate X 509 Certificate From Public Key Online Game
Example
This example assumes that a file named 'test.xml' exists in the same directory as the compiled program. It also assumes that 'test.xml' contains a 'creditcard' element. You can place the following XML into a file called test.xml and use it with this example.
Compiling the Code
To compile this example, you need to include a reference to
System.Security.dll.Include the following namespaces: System.Xml, System.Security.Cryptography, and System.Security.Cryptography.Xml.
.NET Framework Security
The X.509 certificate used in this example is for test purposes only. Applications should use an X.509 certificate generated by a trusted certificate authority or use a certificate generated by the Microsoft Windows Certificate Server.